Overview
I recently set up a dedicated mini PC firewall running pfSense with Mullvad VPN to route all my home network traffic through an encrypted tunnel. This setup provides network-wide privacy protection, eliminates the need for individual device VPN clients, and gives me granular control over my network security.
Bottom line: 937 Mbps download speeds through the VPN with 21ms latency to (XX) servers, all traffic automatically protected, and enterprise-grade firewall features.
Hardware Selection
After researching various options, I chose the HUNSN RS41 Mini PC Firewall Appliance:
- CPU: Intel Celeron N4505 with AES-NI hardware acceleration
- Network: 4x 2.5GbE Intel I226-V ports
- Memory: 8GB RAM
- Storage: 128GB SSD
- Connectivity: Console port, Type-C, HDMI, DP, SIM slot
- Form Factor: Fanless design with heat sink cooling
The AES-NI support was crucial for VPN performance, and the 4x 2.5GbE ports provide room for network expansion.
Cost: EUR 221.41 for the complete firewall appliance - a reasonable investment for enterprise-grade network security.
Physical Hardware Setup
 HUNSN RS41 Mini PC with 4x 2.5GbE ports, fanless design, and multiple connectivity options
HUNSN RS41 Mini PC with 4x 2.5GbE ports, fanless design, and multiple connectivity options
 EIR fiber optic connection providing high-speed internet to the Sagecom router
EIR fiber optic connection providing high-speed internet to the Sagecom router
 EIR Sagecom W7 5G fiber router configured in DMZ mode with pfSense as the designated host
EIR Sagecom W7 5G fiber router configured in DMZ mode with pfSense as the designated host
Network Topology
Internet → ISP Fiber Modem → pfSense Firewall → LAN Devices
↓
[DMZ Configuration]
Reserved IP: 192.168.1.x
↓
[pfSense Routes All Traffic]
↓
Mullvad VPN (XX)
Initial pfSense Configuration
1. Basic Setup
I installed pfSense Plus 23.01 and configured the network interfaces:
- WAN (igc0): DHCP from ISP router (192.168.x.x/24)
- LAN (igc1): Static 10.x.x.1/24 network
- OPT1 (tun_wg0): Mullvad WireGuard tunnel
- OPT2 (igc3): Available for future expansion
2. ISP Router Configuration
On the ISP fiber router:
- Enabled DMZ mode
- Reserved IP for the pfSense WAN interface
- Reduced firewall setting from Medium to Low (since pfSense handles all security)
- This prevents double NAT issues and gives pfSense direct internet access
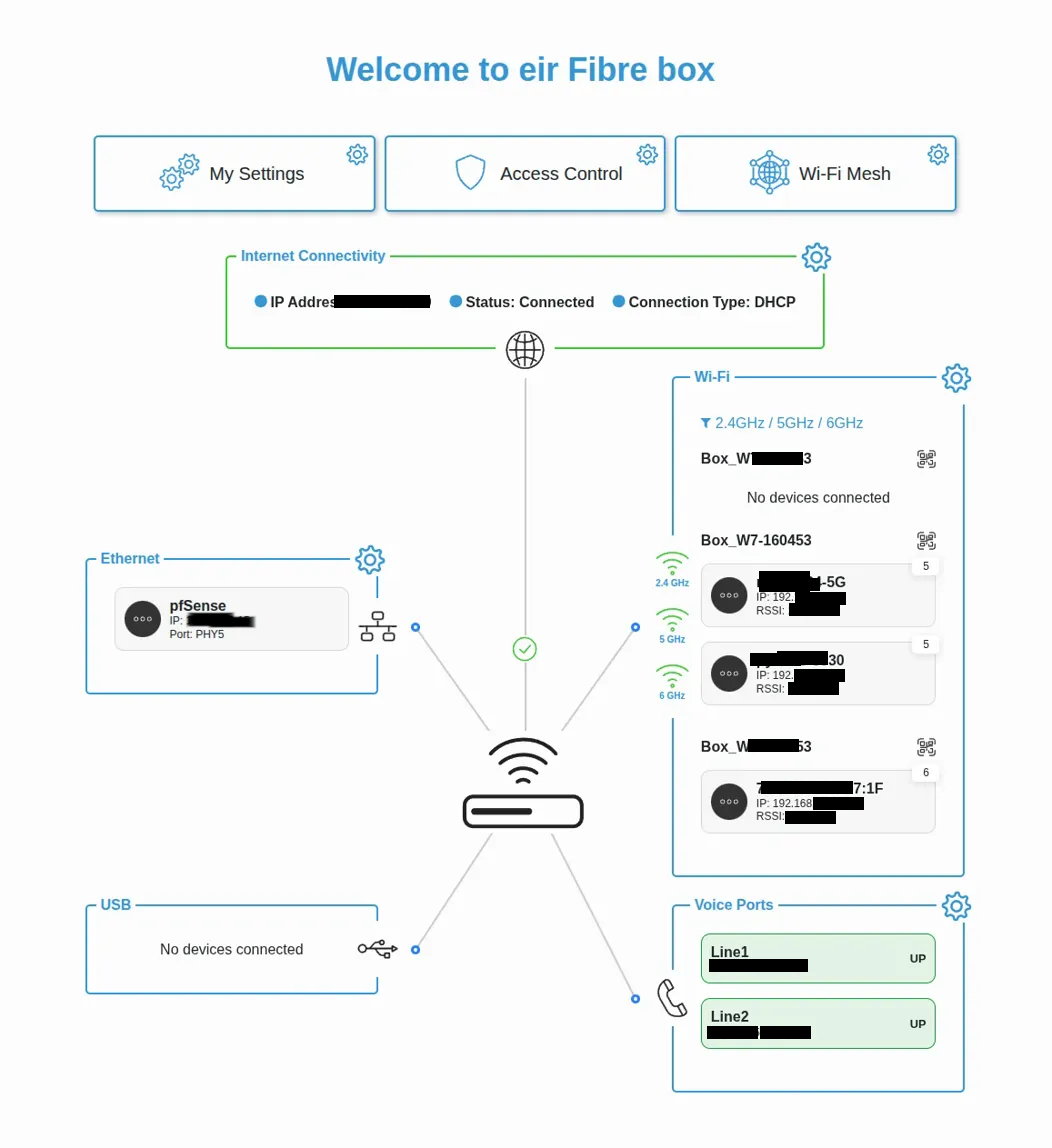 ISP router dashboard showing pfSense connected via Ethernet with reserved IP
ISP router dashboard showing pfSense connected via Ethernet with reserved IP
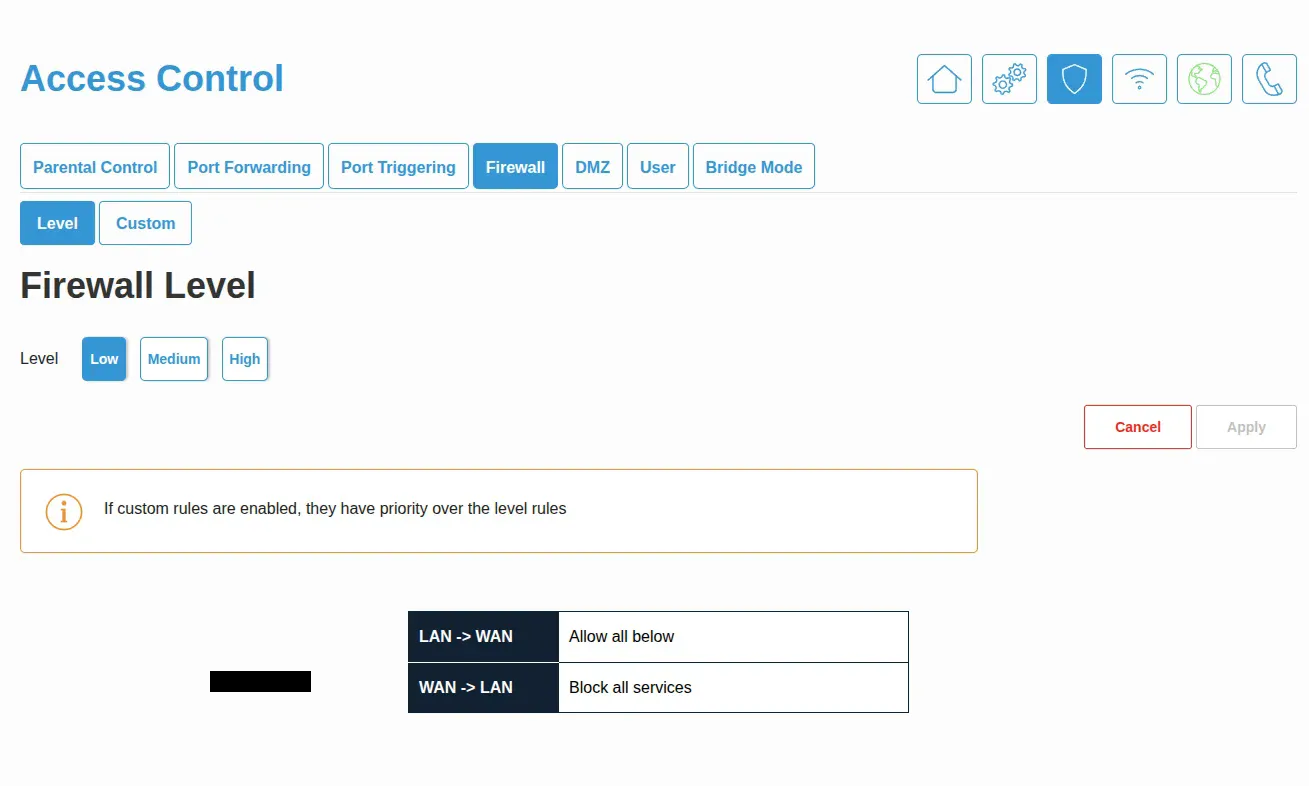
DMZ configuration placing pfSense in the demilitarized zone for direct internet access
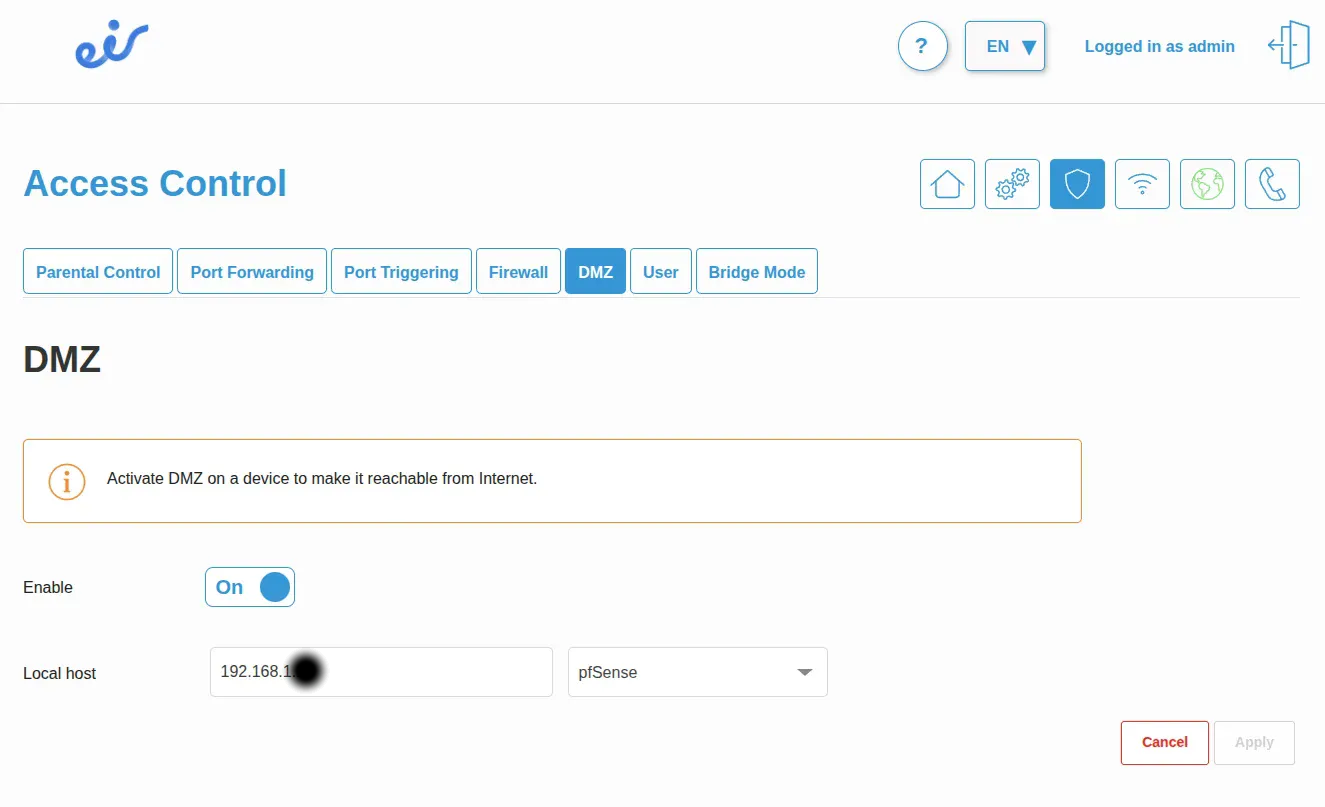 EIR router firewall level set to “Low” since pfSense provides comprehensive security
EIR router firewall level set to “Low” since pfSense provides comprehensive security
Mullvad VPN Integration
1. WireGuard Key Generation
I used Mullvad’s web interface to generate WireGuard keys:
- Created multiple device keys for redundancy
- Selected the (XX) server (location) for optimal latency
- Downloaded the WireGuard configuration for the country of choice
2. pfSense WireGuard Setup
Created a WireGuard tunnel in pfSense:
- Interface: OPT1 (MULLVAD_VPN)
- Tunnel IP: x.x.x.x/32
- Endpoint: (location) x server
- Port: 51820 (UDP)
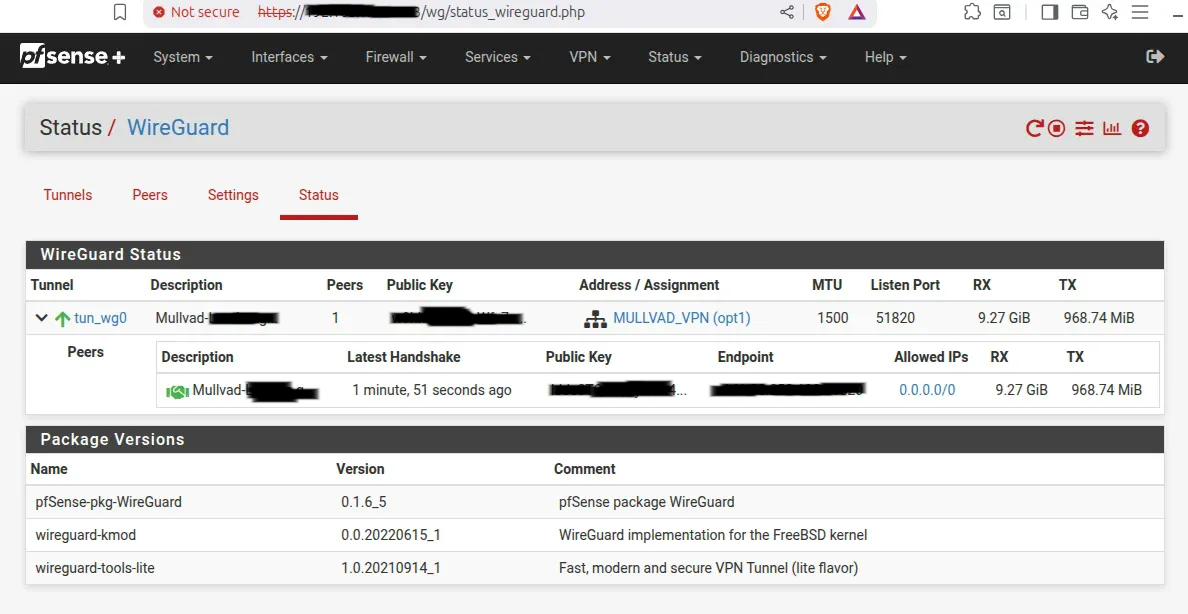 pfSense Plus 23.01 system information showing interface status and hardware details
pfSense Plus 23.01 system information showing interface status and hardware details
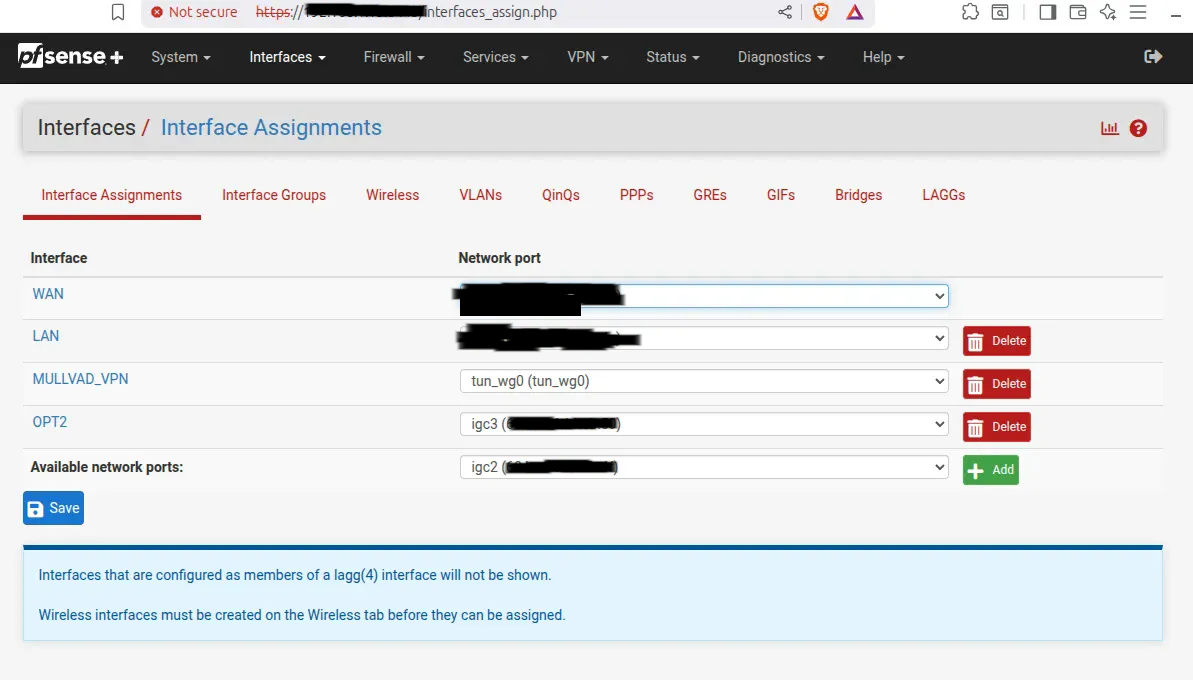 Network interface assignments: WAN (igc0), LAN (igc1), MULLVAD_VPN (tun_wg0), and OPT2 (igc3)
Network interface assignments: WAN (igc0), LAN (igc1), MULLVAD_VPN (tun_wg0), and OPT2 (igc3)
3. DNS Configuration
- Primary DNS: 1.1.1.1 (Cloudflare)
- Secondary DNS: 9.9.9.9 (Quad9)
- DNS Resolver: Enabled on pfSense for local network
I decided on using Cloudlare and Quad9 for the right blend of speed and security
Firewall Rules and Routing
The key to this setup is the policy-based routing configuration: select Hybrid Outbound NAT and create the Mullvad outbound NAT rule as listed in the screenshot below
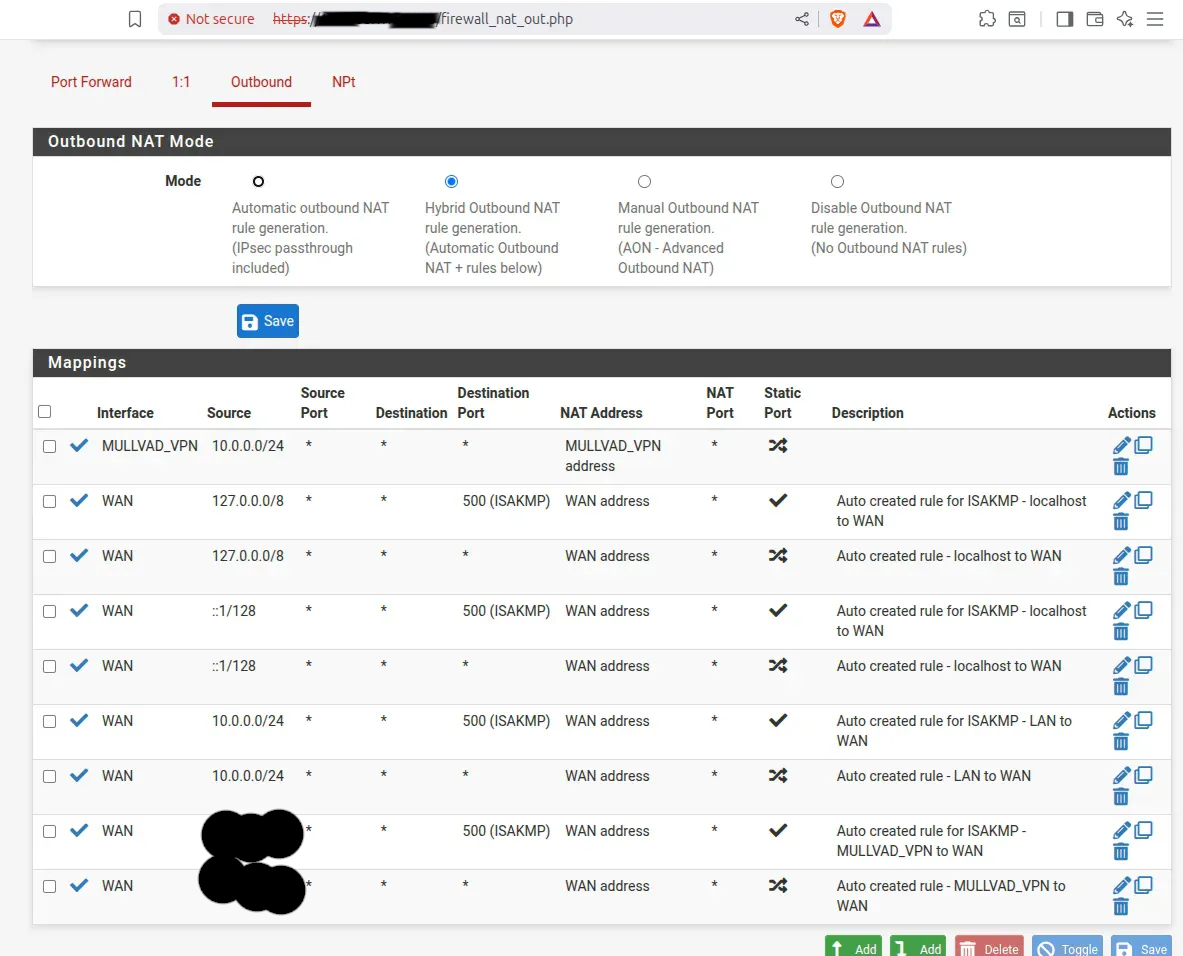 NAT mapping configuration showing automatic outbound rules for MULLVAD_VPN and WAN interfaces
NAT mapping configuration showing automatic outbound rules for MULLVAD_VPN and WAN interfaces
Critical Firewall Rules
| |
Routing Table
Destination Gateway Flags Netif
default 192.168.x.254 UGS igc0
10.x.x.0/24 link#2 U igc1
x.x.x.x (tunnel) link#9 UH lo0
192.168.x.0/24 link#1 U igc0
Performance Results
Speed Test Through VPN
| |
Results:
- Download: 937.12 Mbps
- Upload: 241.35 Mbps
- Latency: 21.01 ms (idle), 104.82 ms (loaded)
- Server: (location) (Airband Community Internet)
- Packet Loss: 0.0%
VPN Verification
| |
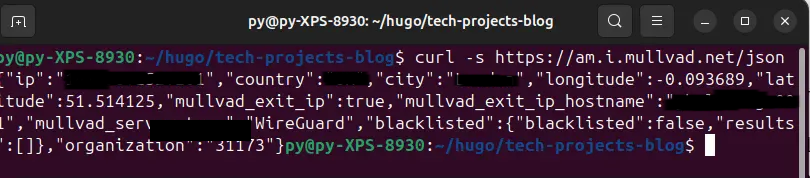 Terminal output confirming all traffic routes through Mullvad’s (XX) (Location) server
Terminal output confirming all traffic routes through Mullvad’s (XX) (Location) server
| |
Client Network Verification
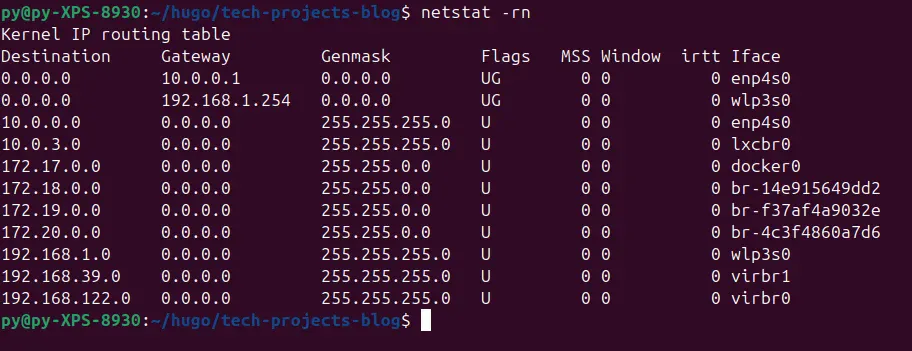 Client device routing table showing traffic properly routed through the pfSense gateway
Client device routing table showing traffic properly routed through the pfSense gateway
Security Features Implemented
Network-Wide Protection
- All devices automatically use VPN without individual clients
- No DNS leaks - all queries go through Mullvad
- Kill switch functionality via firewall rules
Advanced Firewall Rules
- Block IPv4 link-local traffic
- SSH brute force protection (sshguard)
- Port 0 traffic blocking
- Anti-lockout rules for management access
Hardware Security
- AES-NI encryption acceleration
- Dedicated firewall hardware isolated from main systems
- Console port access for emergency management
Lessons Learned
What Worked Well
- Policy-based routing in pfSense is incredibly powerful
- AES-NI hardware acceleration maintains near-native speeds
- DMZ configuration eliminates complex port forwarding
- WireGuard protocol is fast and reliable
Challenges Overcome
- Initially had routing loops - solved with proper gateway assignments
- Had to reserve the DHCP IP on the ISP router to prevent address changes
- Learning pfSense’s rule processing order was crucial
Performance Considerations
- (XX) server selection balanced speed vs latency optimally
- 2.5GbE ports future-proof the setup for faster internet
- Fanless design runs completely silent
Future Expansion Plans
Network Segmentation
- Use OPT2 port for IoT device isolation
- Create VLAN for guest network
- Set up dedicated streaming VLAN with different exit nodes
Monitoring & Analytics
- Implement ntopng for traffic analysis
- Set up Grafana dashboards for network metrics
- Configure log aggregation for security monitoring
High Availability
- Add second pfSense unit for failover
- Implement CARP for automatic failover
- Set up multiple Mullvad exit points
Conclusion
This pfSense + Mullvad setup delivers enterprise-grade network security with impressive performance. Getting 937 Mbps through a VPN tunnel while maintaining sub-25ms latency proves that dedicated hardware and proper configuration can deliver both security and speed.
The policy-based routing ensures all devices are automatically protected without individual VPN clients, and the pfSense firewall provides granular control over network access. The hardware investment pays off in reliability, performance, and future expandability.
Key Takeaways:
- Dedicated firewall hardware > consumer router solutions
- AES-NI acceleration is essential for VPN performance
- Policy routing in pfSense provides ultimate flexibility
- Network-wide VPN protection simplifies device management
Hardware used: HUNSN RS41 with Intel Celeron N4505, 4x 2.5GbE ports, 8GB RAM
Software: pfSense Plus 23.01, Mullvad VPN via WireGuard
Performance: 937 Mbps down / 241 Mbps up through VPN